COMPUTER NETWORKING, Day - 3
Safeguarding Networks: Enhancing Security and Efficiency in the DevOps Landscape
Table of contents
Task - 1: Explore network security fundamentals, including firewalls, VPNs, access control, and encryption.
Network security fundamentals play a crucial role in protecting sensitive data, ensuring the integrity of network communications, and mitigating the risk of unauthorized access or malicious activities. Several key components contribute to a robust network security framework, including firewalls, VPNs, access control, and encryption.
1) Firewalls:
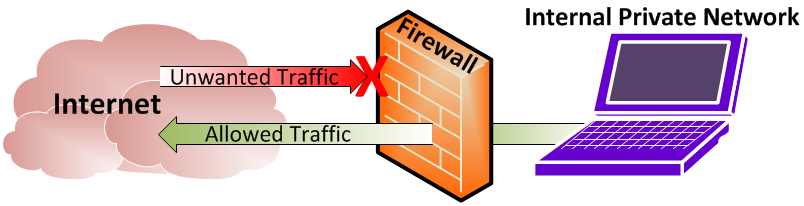
Firewalls act as the first line of defence by monitoring and controlling incoming and outgoing network traffic. They enforce security policies, such as allowing or blocking specific protocols, ports, or IP addresses, to prevent unauthorized access and filter out potential threats.
Example: Firewalls act as digital barriers that monitor and control network traffic, just like a security guard checks IDs before allowing entry to a building.
Here are the key points about firewalls in network security:
Firewalls act as a barrier between trusted internal networks and untrusted external networks.
They monitor and control incoming and outgoing network traffic based on predefined security rules.
Firewalls use packet filtering techniques to examine individual packets of data.
Network Address Translation (NAT) is often used to hide internal IP addresses.
Application-level filtering allows more granular control over traffic.
Stateful inspection keeps track of the state of network connections.
Some firewalls incorporate intrusion prevention systems (IPS) to detect and block known attack patterns.
Firewalls provide a crucial defence against unauthorized access, malware, and threats.
By implementing and properly configuring firewalls, organizations can bolster their network security and protect sensitive data.
2) VPNs (Virtual Private Networks):

VPNs establish secure connections over public networks, enabling users to access private networks remotely. By encrypting data traffic and creating a secure tunnel, VPNs protect sensitive information from interception, ensuring confidentiality and integrity.
Example: VPNs create secure and encrypted connections, similar to using a secret tunnel, allowing users to access private networks remotely.
Here are the key points about VPNs in network security:
Secure remote access to private networks.
Data encryption for confidentiality and integrity.
Tunnelling protocols establish secure connections.
Provides privacy and anonymity by masking IP addresses.
Access control through user authentication and authorization.
Enhances security when using public Wi-Fi networks.
VPNs are crucial for maintaining secure connections, protecting data, and ensuring privacy in network communications.
3) Access Control:

Access control mechanisms limit network access to authorized users and devices. This includes user authentication through strong passwords, multi-factor authentication, and implementing role-based access control (RBAC) to restrict privileges based on user roles and responsibilities.
Example: Access control ensures that only authorized individuals have access to specific resources, similar to using a key card to enter restricted areas in an office building.
Here are the five main points about access control in network security:
User Authentication: Verify user identities through passwords, biometrics, or two-factor authentication.
Authorization and Privilege Management: Grant or deny access based on user roles and permissions.
Network Segmentation: Divide the network into isolated segments to control access and limit breaches.
Access Control Lists (ACLs): Define rules to allow or deny access based on specific criteria.
Secure Remote Access: Implement secure mechanisms (e.g., VPNs) for remote network access.
These points highlight the key aspects of access control, focusing on user authentication, authorization, network segmentation, access control rules, and secure remote access.
4) Encryption:
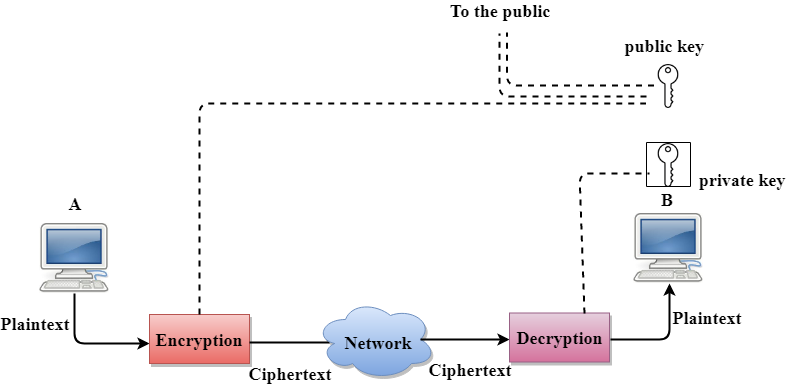
Encryption transforms data into an unreadable format using cryptographic algorithms. It ensures data confidentiality, even if intercepted, by allowing only authorized parties with the corresponding decryption keys to access and decipher the information.
Example: Encryption converts data into a secret code that can only be deciphered using a specific key, like writing a message in a secret language that only the intended recipient can understand.
Here are the five main short points about encryption in network security:
Encryption protects data by converting it into an unreadable format.
Symmetric and asymmetric encryption use keys for encryption and decryption.
Encryption ensures data integrity and detects unauthorized modifications.
TLS/SSL protocols encrypt data during transmission over networks.
Encryption is crucial for data security and compliance with regulations.
By implementing encryption, organizations can secure their data, maintain privacy, ensure integrity, and adhere to compliance standards.
Task -2: Discuss the importance of network security in the DevOps workflow.

Network security plays a critical role in the DevOps workflow, where development and operations teams collaborate to deliver software and services efficiently. Here are several reasons why network security is important in the DevOps workflow:
Protecting Sensitive Data: In the DevOps workflow, sensitive data, such as source code, configuration files, and user information, is shared and accessed by multiple team members. Network security measures, such as encryption and access control, ensure that this sensitive data remains protected from unauthorized access or tampering.
Example: Encrypting customer passwords in a database ensures that even if the database is compromised, the passwords are unreadable and protected.Safeguarding Infrastructure: DevOps relies heavily on cloud services, virtual environments, and containerization technologies. Proper network security measures, including firewalls and VPNs, protect these infrastructure components from potential attacks, ensuring the availability and integrity of the development and production environments.
Example: Using a firewall to block unauthorized access to a server prevents malicious actors from gaining control over the infrastructure and compromising its integrity.Mitigating Security Risks: Continuous Integration and Continuous Deployment (CI/CD) pipelines are core elements of the DevOps workflow. Network security measures help identify and mitigate security vulnerabilities in the pipeline, preventing unauthorized code modifications, injection attacks, or data breaches during the development, testing, and deployment stages.
Example: Running automated vulnerability scans on a web application during the development process identifies and addresses potential security weaknesses before deployment.Ensuring Secure Communication: Collaboration between DevOps teams often involves communication over networks. Network security measures, such as secure protocols, encryption, and secure communication channels, protect sensitive information shared during discussions, code reviews, and deployments.
Example: Using secure protocols like HTTPS when transferring data between a client and a server ensures that the information exchanged is encrypted and cannot be intercepted or tampered with.Compliance and Regulatory Requirements: Many industries have specific compliance and regulatory requirements for data protection. Network security helps ensure compliance with these standards, such as the General Data Protection Regulation (GDPR) or Payment Card Industry Data Security Standard (PCI DSS), by implementing necessary controls, encryption, and access restrictions.
Example: Implementing access controls and audit logs in an application to meet regulatory requirements, such as ensuring only authorized personnel can access sensitive customer data.Early Detection of Threats: DevOps promotes a proactive approach to software development and delivery. Incorporating network security practices, such as network monitoring, intrusion detection systems, and vulnerability assessments, allows for early detection and mitigation of potential threats, minimizing the impact on the development and production environments.
Example: Deploying intrusion detection systems that monitor network traffic can quickly detect and alert on any suspicious activities or potential cyber-attacks.Maintaining Customer Trust: Network security breaches can lead to compromised customer data, financial loss, and reputational damage. By prioritizing network security in the DevOps workflow, organizations demonstrate their commitment to protecting customer information and maintaining trust, which is crucial for sustaining long-term relationships with clients and users.
Example: Regularly updating and patching software vulnerabilities to protect against known exploits, ensuring customer data is secure and maintaining their trust in the organization's services.
Overall, integrating robust network security practices into the DevOps workflow helps ensure the confidentiality, integrity, and availability of systems, data, and services throughout the software development lifecycle. It promotes a secure and resilient environment where development and operations teams can collaborate effectively while protecting sensitive information from potential threats.
Tomorrow we will learn about - Network Devices and Technologies
Thank you so much for reading.
Follow me on LinkedIn to see interesting posts like this : )
